Numerous information-tracking solutions have been implemented worldwide to fight the COVID-19 pandemic. While prior work has heavily explored the factors affecting people’s willingness to adopt contact tracing solutions, numerous countries have implemented other information tracking solutions that use more and more sensitive data.
Continue readingCategory Archives: mobile security and privacy
On Smartphone Users’ Difficulty with Understanding Implicit Authentication
Implicit authentication (IA) has recently become a popular approach for providing physical security on smartphones. It relies on behavioral traits (e.g., gait patterns) for user identification, instead of biometric data or knowledge of a passcode. However, it is not yet known whether users can understand the semantics of this technology well enough to use it properly.
Continue readingIs Implicit Authentication on Smartphones Really Popular?
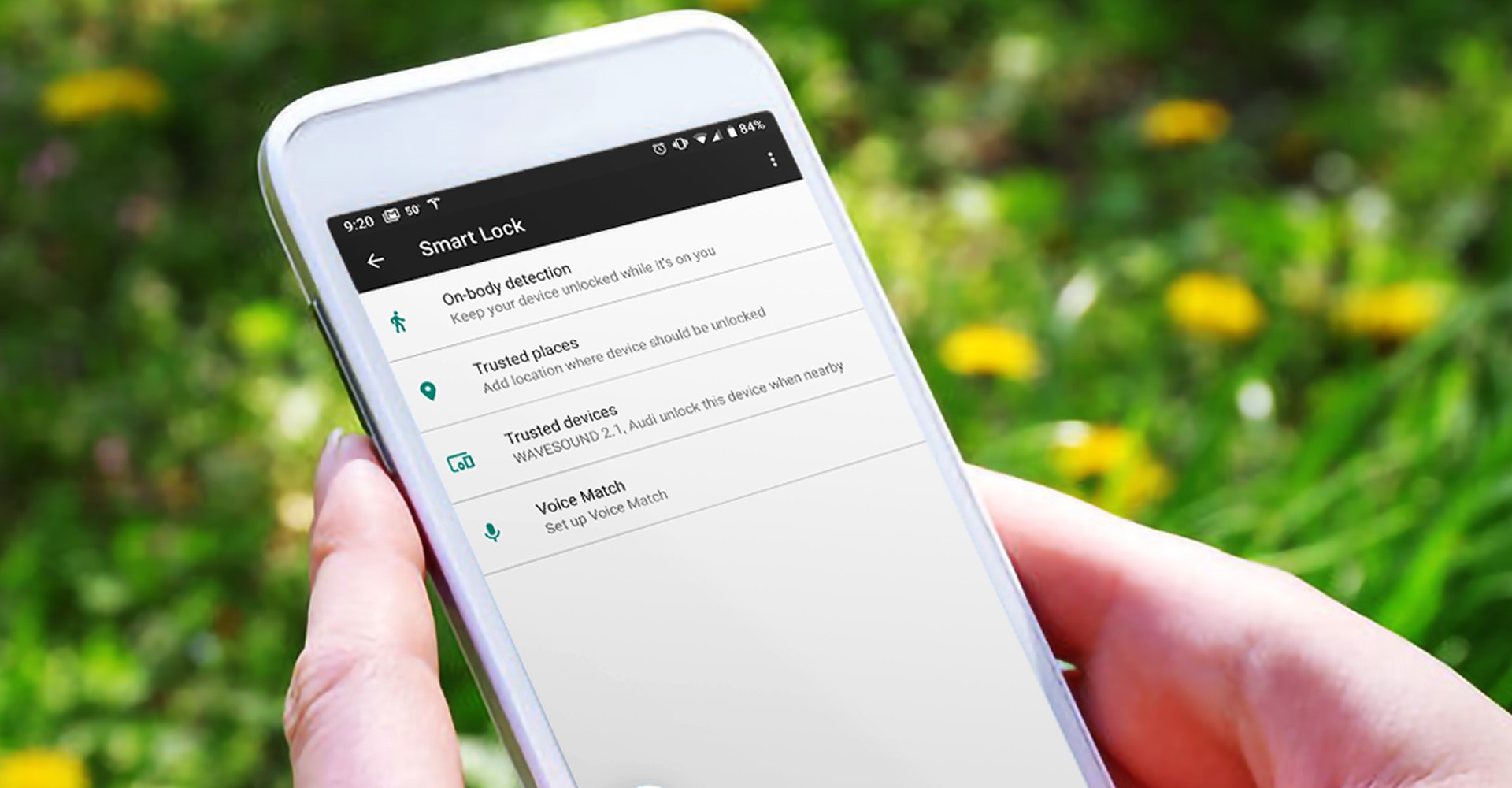
Implicit authentication (IA) on smartphones leverages behavioral and contextual data to identify users without requiring explicit input, and thus can alleviate the burden of smartphone unlocking. In a collaboration with Samsung Research, Masoud Mehrabi Koushki,, a PhD candidate in my research group, has led an exploration of how would smartphone users perceive a commercialized IA scheme in a realistic setting?
Continue readingAge and Smartphone Authentication

Nobody wants to spend time unlocking their phones, particularly when it happens some 50 times a day. This is why both industry and academia have been figuring out how to minimize this unwanted overhead, while still keeping smartphones users secure. To improve the technology, developers need to understand how exactly users use it, what works and what does not, what are the patterns of users’ behaviour with the technology. This is the knowledge gap that LERSSE’s alumni Lina Qiu was working on addressing in her Master’s thesis research. Her research investigated the interplay between age and smartphone authentication behavior.
Continue readingMaking Sense of Unauthorized Access to Smartphones

Unauthorized physical access to personal devices by people known to the owner of the device is a common concern, and a common occurrence. But how do people experience incidents of unauthorized access? Using an online survey, I’ve collaborated with Diogo Marques from the University of Lisbon, his co-supervisors, and my UBC colleague Prof. Ivan Beschastnikh. Diogo led a study, in which he collected 102 accounts of unauthorized access. Participants wrote stories about past situations in which either they accessed the smartphone of someone they know, or someone they know accessed theirs. The findings of the study will be presented in May at ACM SIG CHI conference, the top HCI venue in the world..
Continue readingWhere in Android apps are crypto APIs mis-used?

Recent research suggests that 88% of Android applications that use Java cryptographic APIs make at least one mistake, which results in an insecure implementation. It is unclear, however, if these mistakes originate from code written by application or third-party library developers. Understanding the responsible party for a misuse case is important for vulnerability disclosure. In this paper (presented at ASIACCS ’18), led by LERSSE alumni Ildar Muslukhov, we bridge this knowledge gap and introduce source attribution to the analysis of cryptographic API misuse.
Continue readingSmartphone Users’ Family, Friends, and Other Enemies
 The number of smartphone users worldwide was expected to surpass 2 billion in 2016. To protect personal and other sensitive information from unauthorized access, some smartphone users lock their phones. Yet, others don’t, risking the data and online services accessible through their devices. The risks emanate from both device thieves and those who belong to the users’ social circles, so called social insiders. In 2014, 2.1 million Americans (under 2%) had phones stolen. Continue reading
The number of smartphone users worldwide was expected to surpass 2 billion in 2016. To protect personal and other sensitive information from unauthorized access, some smartphone users lock their phones. Yet, others don’t, risking the data and online services accessible through their devices. The risks emanate from both device thieves and those who belong to the users’ social circles, so called social insiders. In 2014, 2.1 million Americans (under 2%) had phones stolen. Continue reading
Predicting Smartphone Users’ Permission Decisions
 Current smartphone operating systems regulate application permissions by prompting users on an ask-on-first-use basis. Prior research has shown that this method is ineffective because it fails to account for context: the circumstances under which an application first requests access to data may be vastly different than the circumstances under which it subsequently requests access. LERSSE’s Primal is leading the research collaboration with UC Berkeley, in which a longitudinal 131-person field study was performed to analyze the contextuality behind user privacy decisions to regulate access to sensitive resources. Continue reading
Current smartphone operating systems regulate application permissions by prompting users on an ask-on-first-use basis. Prior research has shown that this method is ineffective because it fails to account for context: the circumstances under which an application first requests access to data may be vastly different than the circumstances under which it subsequently requests access. LERSSE’s Primal is leading the research collaboration with UC Berkeley, in which a longitudinal 131-person field study was performed to analyze the contextuality behind user privacy decisions to regulate access to sensitive resources. Continue reading
“I Don’t Use Apple Pay Because It’s Less Secure …”
 This paper reports on why people use, not use, or have stopped using mobile tap-and-pay in stores. The results of our online survey with 349 Apple Pay and 511 Android Pay participants suggest that the top reason for using mobile tap-andpay is usability. Surprisingly, for nonusers of Apple Pay, security was their biggest concern. A common security misconception we found among the nonusers (who stated security as their biggest concern) was that they felt storing card information on their phones is less secure than physically carrying cards inside their wallets. Continue reading
This paper reports on why people use, not use, or have stopped using mobile tap-and-pay in stores. The results of our online survey with 349 Apple Pay and 511 Android Pay participants suggest that the top reason for using mobile tap-andpay is usability. Surprisingly, for nonusers of Apple Pay, security was their biggest concern. A common security misconception we found among the nonusers (who stated security as their biggest concern) was that they felt storing card information on their phones is less secure than physically carrying cards inside their wallets. Continue reading
Social Insider Attacks on Facebook
 Facebook accounts are secured against unauthorized access through passwords and device-level security. Those defenses, however, may not be sufficient to prevent social insider attacks, where attackers know their victims, and gain access to a victim’s account by interacting directly with their device. To characterize these attacks, we ran two MTurk studies. In the first study Continue reading
Facebook accounts are secured against unauthorized access through passwords and device-level security. Those defenses, however, may not be sufficient to prevent social insider attacks, where attackers know their victims, and gain access to a victim’s account by interacting directly with their device. To characterize these attacks, we ran two MTurk studies. In the first study Continue reading


